GOVERNANCE & ACCESS MANAGEMENT
GOVERNANCE + SECURITY
An important part of any security stack
Identity Governance and Access Management is the policy-based centralized orchestration of user identity management and access control. Identity governance helps support enterprise IT security and regulatory compliance. Protecon can help with your implementation of IGA and provide best practices and guidance. Identity Governance (IGA) and Access Management (IAM) is an essential part of enterprise security.
Protecon guides you to deploy best practice IGA through Entra ID Premium

Compromised accounts lead to costly and devastating consequences. Identity Access Management (IAM) and data governance is the solution.
Quick Services Overview
- Identity Overview
- Mergers, Acquisitions & Divestitures
- Hybrid Identity
- Identity Governance
- Identity and Access Management
- Workday to Entra ID Provisioning
- Identity Provisioning
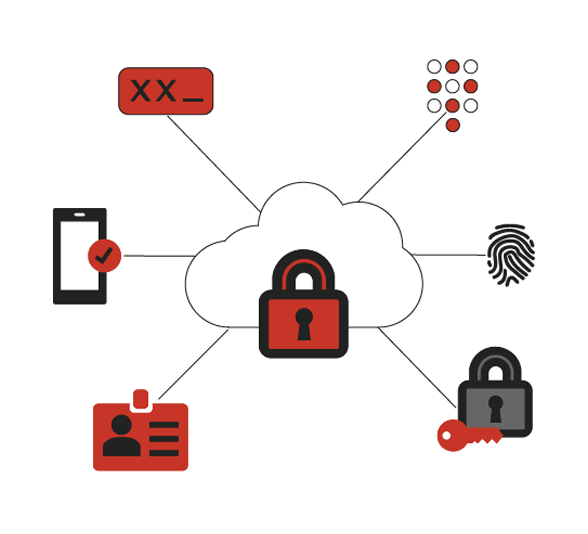
Identity, Identity, Identity
This is the control plane to access your corporate data. Without a secure identity, access to your data is at risk of being ex-filtrated and used to subvert your business.
Microsoft Entra ID has you covered. With state of the art security controls to allow you to give or restrict access based on conditions, 2 factor authentication or the risk score of the user signing in.
Find out what Protecon has to offer in the identity space and how we can get you secure!
Are you excited? Did you just acquire a company to advance your brand and market strategy?
Once the excitement has diminished, now you have to get everything to work together by integrating another companies culture into your own. The first step is to incorporate that companies’ infrastructure into your own and give your new employees access to their new companies resources.
You will need to apply your set of identity security practices and migrate them into your environment. This is the most important part of any Merger, Acquisition or divestiture. Don’t put identity at the bottom of priorities.
Protecon has strategies and best practices to enable you to get the job done efficiently and with low user impact. Talk to us today about the benefits of using Protecon for your M.A.D. project.
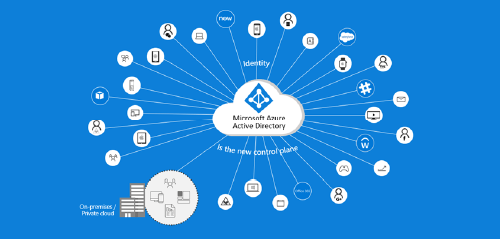
Identities in the Cloud are the future, however what can you do until you get there?
Microsoft’s identity solutions span on-premises and cloud-based capabilities, creating a single user identity for authentication and authorization to all resources, regardless of location.
But what about the pesky alternate IDs, what do you do with those? Most companies will begrudgingly configure ADFS for this scenario to maintain normalcy in their environment, but there are overhead costs associated with this. Protecon has developed a solution to customize the sign in experience to enable this scenario utilizing Entra ID authentication and allowing users to continue to use of the alternate id solution. Same Identity, same sign on to all cloud based and on-premises based applications.
Protecon can make your hybrid identity solution configuration easy. Ask us how!

"Who accessed what and when?"
Are you aware of what your users are looking at and accessing on a regular basis? Do you have control in place to restrict access to systems or other forms of data?
Identity governance answers the who, what, where, why and how your users gain access to applications and data and if they can or should. You don’t want your company to become the one where data was leaked that was detrimental to your business.
Let Protecon show you the way, or at least get you there!
Do you have a gatekeeper to your environment?
The Entra ID platform provide the ability to restrict access, require Two-Factor authentication, provide risk assessments of users, allow self service and much more.
Entra ID Premium allows you to provide conditional access to to your applications, whether in the cloud or on-premises giving you peace of mind. Connectivity is a cinch with all the standard authentication protocols and cloud proxy.
Protecon has been in this space for a long time. We have a set of standard best practices that many of our customers use on a regular basis to secure their environment. We help you to architect your identity security solution for every scenario.
Get in touch with us today to secure access for your company's IP!

New to Workday? Have a deeply integrated Workday solution that needs to be migrated to Entra ID
Protecon has robust experience with Workday provisioning in Entra ID. Through previous complex provisioning scenarios, we have mastered the flows needed to have solid data in the cloud and on premises.
Single tenant, multi-tenant, mixed environment scenarios? We have seen it all and can assist you in making an easy transition to Entra ID for your identity provisioning needs.
Let Protecon take care of your configuration for Workday Provisioning!
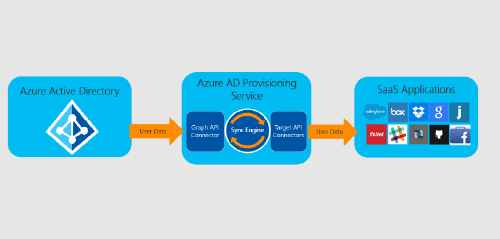
Want to automate user account creating in your SaaS applications using your existing Identity?
There are a lot of applications that can utilize the SCIM protocol to automatically provision users into applications. Some even have it built into Entra ID applications. This leaves little to customization or to be able to scale for a large amount of applications.
Protecon has in depth knowledge of the SCIM protocol and the Entra ID provisioning engine to accurately set up and configure applications for automatic provisioning if said applications support it. Custom attribute passing, dynamic user assignment and Just-in-Time adding or removing users makes on-boarding and off-boarding a cinch.


